|
From CertCities.com
|
||
|
PopQuiz Microsoft Exam #70-081: Implementing and Supporting Exchange Server 5.5 6 questions. Answers can be found at the end of the quiz. courtesy of Transcender LLC Questions 1. The Microsoft Exchange Server organization at Martin's company consists of four Microsoft Exchange Server computers that are distributed across three sites. SERVERA and SERVERB are in the Nashville site. SERVERC is located in the Seattle site. SERVERD is in the Austin site. SERVERB contains a public folder named NOTICES and replicates its contents to the three other servers. The public folder affinity value has been set to 10 for the Seattle site and 50 for the Austin site. SERVERA hosts Martin's mailbox and serves as his public folder hierarchy server. He logs on to SERVERA and tries to access a document stored in NOTICES. In what order will Microsoft Exchange Server access the servers when attempting to connect Martin to NOTICES? (Select the best choice.)
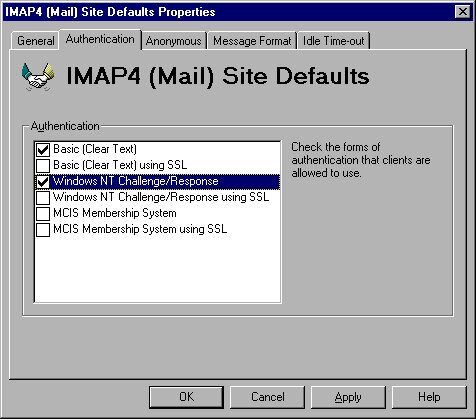
2. Ray has installed a Microsoft Exchange Server on the corporate LAN. To protect the corporate network from unauthorized access, Ray is configuring a firewall. He wants to provide support to remote employees using IMAP4 clients over the Internet. Ray has enabled IMAP4 and configured the Authentication tab as shown below.
What TCP ports must Ray enable the remote users to access? (Select all choices that are correct.)
3. Frank must back up a Microsoft Exchange Server computer. The transaction logs and the database files are located on different hard disks. He disables circular logging and makes a normal backup on Friday night and incremental backups every night, Monday through Thursday. The hard disk containing the information store fails at 4 p.m. on Tuesday afternoon. Up to what point in time can Frank recover the data? (Select the best choice.)
4. Lou is a Microsoft Exchange Server administrator for a large company that is divided into three sites: SITE01, SITE02 and SITE03. He has configured 56-Kbps links between the sites and X.400 Connectors to facilitate message transfers. Directory replication occurs between Microsoft Exchange Server computers in the three sites. What should Lou do to improve server response times and minimize intersite network traffic? (Select all choices that are correct.)
5. Adrian configures the corporate Microsoft Exchange Server computer with a three-day deleted item retention time for all deleted items. She performs a full backup on this server every Thursday evening. What should Adrian do to enable users to recover deleted e-mail messages after the retention period expires? (Select the best choice.)
6. A Microsoft Exchange Server computer in one of your corporate offices functions as an Internet messaging system for the organization. You have also installed IIS on the computer to enable FTP transmissions. You have set up a firewall to protect the corporate network and enabled access to a minimal number of ports. Required result: Optional desired results: Proposed solution: Which results does the proposed solution produce? (Select the best choice.)
Answers: 1) Choice b is correct. When attempting to connect Martin to NOTICES, Microsoft Exchange Server will access the servers in the following order: SERVERA, SERVERB, SERVERC and then SERVERD. This is because the information store will initially attempt to connect to Martin's public folder server, SERVERA. If, for some reason, the attempt is unsuccessful, then Microsoft Exchange Server will randomly attempt to connect to the other servers at the site that contain a replica of NOTICES. If Microsoft Exchange Server cannot make an intrasite connection, then it will try to connect in increasing order of affinity to the servers in connected sites. Reference: RKG, Ch. 4, Locating Folders by Using Affinities, pp. 72-73. 2) Only choices a and c are correct. To enable the remote employees to access their Microsoft Exchange Server mailboxes using IMAP4 clients over the Internet, Ray must configure the firewall to allow TCP traffic to port 143. To enable the remote employees to send e-mail messages to Internet users, Ray must allow SMTP traffic (TCP port 25) to pass through the firewall. Port 80 is the default port for HTTP, and port 993 is used for an SSL-encrypted channel. Reference: Operations, Ch. 15, IMAP4, pp. 415-421. 3) Choice d is correct. Frank can recover data to the state that it was in at 4 p.m. on Tuesday. To do so, Frank must first replace the failed hard disk and then restore the information store, directory database and transaction logs from the full backup tape. This restores data to the state that it was in on the previous Friday night when Frank performed the last full backup. To restore the transaction logs to the state they were in as of the Monday night backup, Frank must restore data from the incremental backup tape that he created on Monday. To preserve the existing transaction logs when performing the restore, Frank must disable the Erase All Existing Data option. When the directory service starts, Microsoft Exchange Server will play back the transaction logs and restore the data to the state it was in immediately before the hard disk failed. A normal, or full, backup writes the information store, directory database and transaction logs to tape and then purges the log files. A differential backup writes only the transaction logs to tape and does not purge the log files. An incremental backup writes only new transaction logs to tape and then purges the log files that contain transactions that have already been committed to the database. Differential and incremental backups are only possible if circular logging is disabled. Reference: RKGS, Ch. 4, Backup Types, pp. 89-91; RKGS, Ch. 4, Transaction Logs Recovery, p. 96. 4) Only choices a and c are correct. To improve server response times and minimize intersite network traffic, Lou should schedule directory replication to occur after business hours and configure SITE02 and SITE03 to replicate with SITE01. Directory replication between Microsoft Exchange Server computers within the same site occurs every five minutes. Directory replication between sites can be scheduled to occur during non-peak hours, which enables the Microsoft Exchange Server computers to be fully available to users during the workday when most messaging activity takes place. Configuring directory replication to occur only between SITE02 and SITE03 on one side and SITE01 on the other maintains current directory information within the sites and leaves the 56-Kbps link between SITE02 and SITE03 available for other purposes. To perform intersite directory replication, Lou must first establish messaging connectivity between the sites. He must also configure a Directory Replication Connector to use this messaging connectivity to send update requests to a designated bridgehead server at another site and receive directory changes. Lou can only configure Site Connectors to connect Microsoft Exchange Server sites that are either located on the same LAN or connected by high-bandwidth permanent WAN links. The minimum acceptable bandwidth for using RPCs with Microsoft Exchange Server is 64Kbps. Reference: GS, Ch. 10, Replicating Directory Information, pp. 163-172. 5) Choice c is correct. To enable users to recover deleted e-mail messages after the three-day retention time set for the private information store expires, Adrian should select the Don't Permanently Delete Items Until The Store Has Been Backed Up option on the General page of the Private Information Store Properties sheet. After she configures the retention time for deleted e-mail messages, Microsoft Exchange Server flags deleted e-mail messages as hidden. These e-mail messages remain hidden until their retention time expires. If Adrian selects the Don't Permanently Delete Items Until The Store Has Been Backed Up option, then deleted e-mail messages are kept even after their retention time expires until she backs up the private information store. To recover deleted e-mail messages, users should start Microsoft Outlook version 8.03 or later and select Recover Deleted Items from the Tools menu. Creating an .ost file or a personal folder file to recover the e-mail messages does not produce the required result. Reference: GS, Ch. 8, Information Store, pp. 119-122; Admin.hlp, Find, "General (Private Information Store)," "Deleted Item Retention Time." 6) Choice a is correct. Allowing connections to TCP ports 110 and 25 through the firewall enables the remote employees to use POP3 to access their Microsoft Exchange Server mailboxes and SMTP to send Internet e-mail messages. You produce the first optional desired result by configuring Secure Sockets Layer (SSL) connections, enabling SSL traffic to pass through the firewall, granting Administrator permissions for the local computer to the service account that is used by Microsoft Exchange Server and requiring SSL authentication for all POP3 connections to Microsoft Exchange Server. You achieve the second optional desired result by enabling anonymous LDAP access and permitting LDAP traffic to pass through the firewall. Reference: TechNet, Query, "MS Exchange Server Internet Connectivity and Security," "Exchange Product Facts"; Operations, Ch. 14, Authentication, pp. 399-402. These questions and answers are provided by Transcender LLC. Order the full version of this exam simulation online at www.transcender.com, phone 615-726-8779, 8 a.m. - 6 p.m., (CST), M - F, fax 615-726-8884, or mail to Transcender LLC, 565 Marriott Drive, Suite 300, Nashville, TN 37214. More Pop Quiz: |
||
|
top Copyright 2000-2009, 101communications LLC. See our Privacy Policy. For more information, e-mail . |