4/5/2001 -- In homogeneous Windows 2000 networks (including Win2K Server and Professional), Group Policy allows you to install software, set security and manage settings. So let's dig in and launch the Group Policy snap-in, similar to Figure 1. This is accomplished by clicking Start | Programs | Administrative Tools | Active Directory Users and Computers and right-clicking on the domain or an organizational unit. Select Properties, click the Group Policy tab, and click either New or Edit a Group Policy Object (GPO).
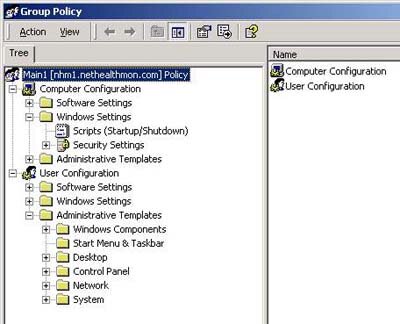 |
| Figure 1. Both the Computer Configuration and User Configuration objects display the Windows Settings and Administrative Templates folders. |
Note: It's important to remember that the Computer Configuration object configures the machine. And as you'd expect, the User Configuration object configures based on the user's logon name. While this seems obvious, it's critical to understanding the forthcoming discussion. Windows Settings
Under the Computer Configuration object, Windows Settings has two objects:
-
Scripts (Startup/Shutdown) -- This is where you can designate scripts, ranging from simple to complex, to run at either the startup or the shutdown of the machine. For more information on scripting, be sure to read Chris Brooke's monthly column, "Scripting for MCSEs," in MCP Magazine.
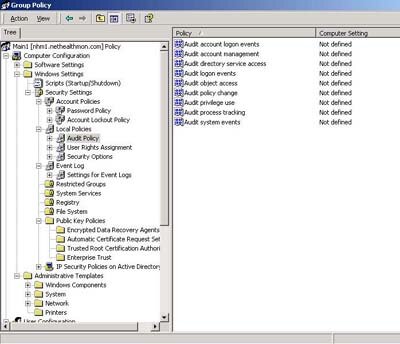
- Security Settings -- Now we can have some fun. If you look at Figure 2, you'll see that the Security Settings object is "rich." As you can see in the right pane of Figure 2, this is where you'd set the ability to audit logon activity on machines that fall under the authority of this GPO.
|
| Figure 2. Take a moment to appreciate the depth of the settings in Security Settings object. (Click image to view larger version.) |
Note: To audit logon activity on the network and have it appear in the server's Event Viewer in the Security Log, you need to set the Local Security Policy snap-in that's accessed from Start | Programs | Administrative Tools | Local Security Policy.
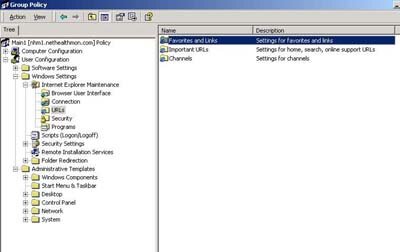
Under the User Configuration object, the Windows Settings folder looks slightly different when you expand it. As seen in Figure 3, there are three selections in addition to what you saw above with the Computer Configuration object.
- Internet Explorer Maintenance. This is a group of settings you can use to enforce your company's Internet policy. For example, you can impose proxy server settings. You can also dictate what URLs are listed under the Favorites folder for each user and what the default home page is (such as the company Web site) at startup.
- Remote Installation Services. On a per-user basis, you can configure on-screen options that relate to automatic and custom setups.
- Folder Redirection. When discussing what can and can't be accomplished with Group Policy, the area of folder redirection emerges as one of the most popular. This is because both IT and business management see great value in enforcing the storage of data on a server upon which regular backups occur and security can be imposed. You start this process by configuring folder redirection so data is moved to the server.
|
| Figure 3. Note that there are three additional selections in the Windows Setting folder under the User Configuration object that aren't found under the Computer Configuration object. (Click image to view larger version.) |
Administrative Templates
Next up are the Administrative Templates. Here you can set hundreds of settings using Group Policy. In fact, this is many people's perception of what Group Policy is -- detailed management via these configurations at the computer and user levels.
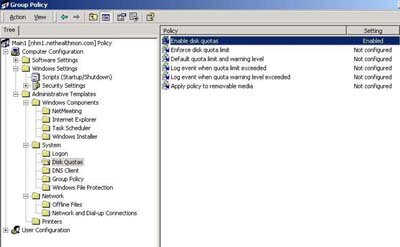
The Administrative Templates under the Computer Configuration object, seen in Figure 4, contains the following folders. (Note that I'm making select comments about the types of configurations possibilities because there are far too many for individual discussion in a column.)
Note: I've always felt a book should be written about Group Policy, which is exactly what MCP Magazine writer Jeremy Moskowitz has done. His book, Windows 2000 System and Group Policies (Sybex, ISBN 0782128815) will be out in mid-August 2001.
|
| Figure 4. The Administrative Templates under the Computer Configuration object contain folders that allow you to make changes to a variety of settings. (Click image to view larger version.) |
- Windows Components. The Windows Components folder contains sub-folders for NetMeeting, Internet Explorer, Task Scheduler and Windows Installer. For example, under NetMeeting, you can use Group Policy to disable remote desktop sharing, a capability I view as security-related. Under the Internet Explorer folder, you may make proxy server settings on a per-machine basis (unlike the per-machine basis I discussed a few paragraphs above).
An administrator might disable the ability to run tasks on an individual machine via the Task Scheduler folder. Here's an interesting example: On a per-machine basis, under the Windows Installer folder, you can have applications installed with elevated privileges so that the user who logs on doesn't have to be a member of the Local Administrators group for an application to automatically install via Group Policy. This is helpful, as you often don't want a "normal" user at a workstation to be a member of the Local Administrators group.
- System. This includes sub-folders for Logon, Disk Quotas, DNS Client, Group Policy and Windows File Protection. Under Logon, you can have Win2K advise the user when a slow network link is detected. Under Disk Quotas you may enable and enforce disk quotas on a per-machine basis. The DNS Client folder allows you to make one policy configuration to set the DNS suffix (note that make DNS-type settings can be made with a DHCP IP address lease, not Group Policy, so don't worry!).
The Group Policy folder allows you to select the order in which policies are processed. And, as a final example for the System folder, the Windows File Protection folder allows you to, not surprisingly, configure Windows File Protection (such as hide the file scan progress window).
- Network. The Network folder allows you to configure, among other things, the use of Offline Folders (something that many people find cool in Win2K and replaces the "Briefcase" application from prior Windows operating systems).
- Printers. Printers allows the publishing of printers to Active Directory and several other printer-related settings.
The Administrative Templates under User Configuration are similar to those listed immediately above, except that the settings are applied on a per-user basis (not per computer).
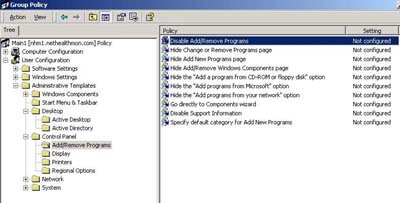
Note: There are minute (or detailed) differences between computer and user, so I highly recommend you take an afternoon off of work some day, take a Win2K Server out to a local park, site in the sun and poke around discovering what these differences are. There are a couple of additional Administrative Template folders under User Configuration that aren't found elsewhere. These are shown in Figure 5.
|
| Figure 5. Some of the sub-folders under Administrative Templates under the User Configuration object aren't found anywhere else. (Click image to view larger version.) |
- Start Menu and Task Bar. One setting you can invoke here (of many possibilities) is to disable changes to the Taskbar and Start Menu Settings. This translates into one less Help Desk call from a user that "something changed."
- Desktop. This folder primarily relates to the management of user interface elements. One setting from the multitude of selections is to enable Active Desktop (one-click functionality and so on).
- Control Panel. This folder contains several sub-folders, including Add/Remove Programs, Display, Printers and Regional Options. While I don't really care as much if users change their time zone via Regional Settings (although I can block that behavior), I'm very interested in the ability to disable Add/Remove Programs so users can't install the latest TurboTax upgrade on a company computer.
Something that many people don't realize is that, if you right-click on any policy and select Properties, then Explain, you'll get an eye full of well-written text that discusses the specific policy. An example of this is shown in Figure 6.
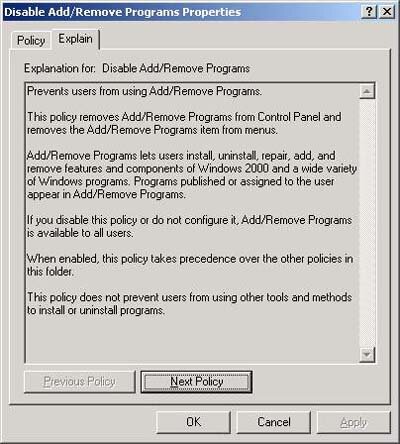 |
| Figure 6. You'll appreciate the explanation provided for each policy in Group Policy. |
If you want more on group policy, there are two cools tools I found at the Microsoft site dedicated to the Win2K Resource Kit (www.reskit.com), where you will click on the "Free Downloads" link.
- Gptool.exe. This tool (Group Policy Verification Tool) is, quite frankly, for large enterprise accounts with multiple sites. It allows administrators to check Group Policy object integrity and monitor policy replication.
- GPresult.exe. This is my favorite Group Policy tool, officially called Group Policy Results. This displays information about the effect that Group Policy has had on the current computer and logged-on user.
Next month I'll revisit Active Directory and dispute the myth in MCSE-land that it should be renamed "Inactive Directory."
Copyright 2001 MCPMag.com. Reprinted with permission.
|

 Column Story
Column Story






